Metasploit — Pivoting
What is Pivoting?
Pivoting is the unique technique of using an instance (also referred to as a ‘plant’ or ‘foothold’) to be able to move around inside a network. Basically using the first compromise to allow and even aid in the compromise of other otherwise inaccessible systems. In this scenario, we will be using it for routing traffic from a normally non-routable network.
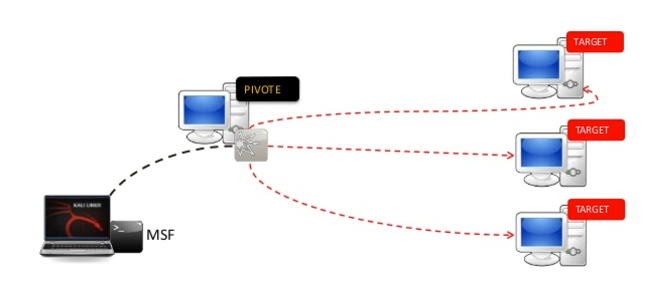
Let’s ditch the theory and go to the DIY tutorial:
For the Lab Set up, We need 3 Virtual machines:
I am taking the machines as follows:
1. Kali (Attacker): 192.168.1.35
2. Windows Bad blue enterprise edition(Foothold/Exposed to the internet):192.168.1.34
3. Windows Bad blue 2(Target machine/on the internal network): 10.10.10.5.
Now
What we are going to do is.. we are going to first compromise the
windows bad blue machine since it is exposed to the internet.
IP of the Windows bad blue machine is 192.168.1.34

So Now our primary target is this machine after that we can use this windows machine as a foothold to compromise the machines in its internal network.
Cool, Let’s fire up our BFF Metasploit and search for bad blue.
We need the 2.72b one.
use the exploit.
show options
set RHOST Victim’s IP.
Hit run or exploit.


Cool we got meterpreter on the box.
Now we need to get details of all the interfaces in the compromised machine’s network.


We can see there is 1 more network interface 10.10.10.3
Now this one seems interesting, let’s take a look into what other machines are connected to it.
Forgetting all the Machines connected to this compromised bad blue machine we need to run arp_scanner on the internal network from IP 10.10.10.1–255
Cool let’s see what we get from our arp_scanner.
command: run arp_scanner 10.10.10.0/24

10.10.10.1 is network address and 10.10.10.255 is broadcast address.
10.10.10.3 is our compromised machine’s internal network’s IP, and the remaining is 10.10.10.5
Now we know our target as 10.10.10.5
Let’s add a route now,

Now let’s do port forwarding.

Now background this session using ctrl+Z or simply type background.
Now since we already know that our machine is vulnerable to bad blue we will use the same exploit otherwise you need to run Nmap scan and enumerate service and their exploits.
Anyway I will just show of quick map demo how you are going to do in practical life.

If you pay attention we have scanned our own system(The IP is of my Kali machine i.e., attacker’s Machine) right?
Yes,
Coz we have already done the port forwarding and any exploit we are
going to do on the 192.168.1.35(Attacker’s Machine) will be forwarded to
10.10.10.5 (The machine inside the network)
Anyway, Let’s go back to our buddy Metasploit.
Since we already know that our target Machine is bad blue vulnerable we are just doing show options with the same exploit.

But here comes the trick,
Now to exploit 10.10.10.5 we need to interchange it with the attacker’s IP i.e., 192.168.1.35 and the RPORT to 9999
and
LHOST won’t remain our attacker’s IP now we need to replace it to the
first compromised Windows machine’s IP since the target machine won’t
understand our attacker’s IP address and can’t connnect to us.
So set RHOST to 10.10.10.3
and RPORT let it be the same.

Cool, let’s run the exploit

Let’s do sysinfo on it:

Bingo.
Now let’s take a look at the active sessions:

Comments
Post a Comment